While it is widely understood that mobile devices are more than just phones – they are a lifeline to the outside world, entertainment platform, GPS system, little black book and a shopping and banking tool – it’s lesser known that these devices are also gateways. Mobile devices can be used by a hacker as an access point into many other aspects of your digital life as well the lives of others in your network, making mobile security about more than just protecting your phone.
Hackers can use your mobile device as an access point to data that have historically been exclusively stored to your laptop or desktop, such as social network and bank accounts. One of the most harmful (and popular) mobile threats has to do with apps. Installing apps from unknown or untrusted sources like apps outside the official Google Play Market could allow hackers to steal sensitive and private information stored on your mobile device including passwords, photos, contacts and location data.
=============================================
Gust MEES
Critical Thinking: "While it is widely understood that mobile devices are more than just phones", really!?? Most people still think that it is ONLY a phone, but in reality it is a mini computer with phone capabilities! And any computer is vulnerable and at risk!!!
Check out also:
- http://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/
Especially check the video under this topic "Ever thought about that your smartphone is also a computer with phone capabilities?" to understand!
=============================================
Read more, a MUST:
http://blogs.mcafee.com/consumer/mobile-devices-the-gateway-for-hackers-to-your-digital-identity?utm_source=twitterfeed&utm_medium=twitter
Via
Gust MEES



 Your new post is loading...
Your new post is loading...





![Why You Should Care About Mobile Security [Infographic] | Latest Social Media News | Scoop.it](https://img.scoop.it/eCYKbrsHLFNXs4GayRTQ8zl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



![Why You Should Care About Mobile Security [INFOGRAPHIC] | Latest Social Media News | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



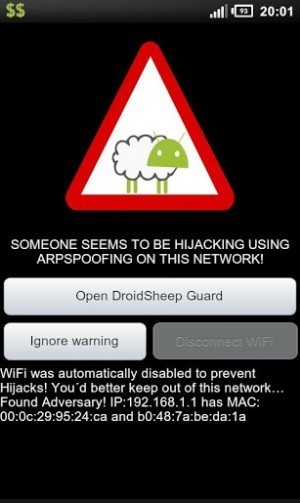
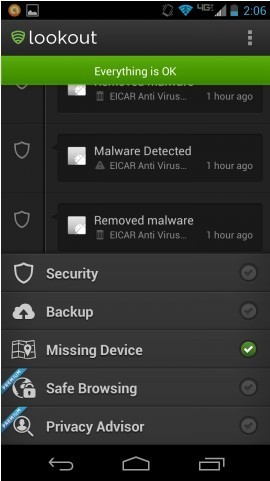
===> making sure that the Android system setting ‘Unknown sources’ is unchecked to prevent dropped or drive-by-download app installs and installing security apps like Lookout to as their first line of defense against malware. <===
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
===> making sure that the Android system setting ‘Unknown sources’ is unchecked to prevent dropped or drive-by-download app installs and installing security apps like Lookout to as their first line of defense against malware. <===
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free